Introduction
Keys in DBMS the primary goal of a Database Management System is supplying a means to keep up and retrieve database info that’s both efficient and convenient.
A key element is a field, or a mixture of fields, in a data source table used to access and sort rows in the tables. Keys are identified to accelerate access to information and, in cases that are many, to produce links between several tables. Keys in DBMS might be either a mix of over one attribute (or columns) or simply a single feature. The primary motive of this’s giving each record a distinctive identity.
What are the Keys in DBMS?
The keys in DBMS are a set or a characteristic pair of characteristics that assist in exclusively determining a tuple (or row) of a relation (or even table). Keys are usually utilized to build relationships between the various tables and columns of a relational database. Specific values in a vital are known as main values.
A database management system (or DBMS) is basically nothing much more than a computerized data-keeping phone system. Owners of the device are provided facilities to do a number of sorts of operations on such a method for both manipulations of the information in the control or the database of the database system itself.
Keys in DBMS
-
Hierarchical DBMS
Working in a format that is based on the product of the parent-child tree, hierarchical DBMS in keys in DBMS are very great for saving info with products that describe characteristics, characteristics, and any other such items. -
Network DBMS
Similar to hierarchical DBMS, this particular method has numerous parents to a lot of relation models. The networking version structure uses SQL because of the manipulation of information which could in turn be implemented to acquire valuable insights and learnings. -
Relational DBMS
One of the more famous DBMS, offered in the marketplace is known as relation DBMS since they’re super easy and very simple to use. These methods are normalized by using information that is commonly saved in tables. -
Object-Oriented DBMS
Objective-oriented DBMS of several structures that are rather extensive in nature. This particular design is based on the performance that information and its concerning object are viewed as a single device.
What exactly are Keys in DBMS?
KEYS in DBMS is a characteristic or a set of attributes that allow you to determine a row(tuple) in a relation(table). They let you search for the relation between the 2 tables. Keys help you exclusively recognize a row at a table by a mix of one or more columns in this table.
Role of Keys in DBMS

Keys in DBMS allow the sharing of details in the database among many apps or people to provide drivers with a single all-encompassing details repository, keys in DBMS play a crucial role.
The keys in DBMS serve as the intermediary between the user and the database. A DBMS provides his roles such as
- Improved data sharing
- Improved data security
- Better data integration
- Improved data access
- Increased user productivity
Characteristics of DBMS

Qualities of DBMS (Database Management System) Real-life Entity. Self Explaining Nature. Atomicity of Operations (Transactions) Concurrent Access with no Anomalies. One of the more basic attributes of the database strategy would be that the database structure contains not just the database itself but additionally, a whole characterization or explanation of the database framework and constraints also referred to as metadata of the database.
- Real-World Entity: DBMS nowadays is real-world and realistic very entities are accustomed to structure its architecture. Also, behavior & attribute characteristics are utilized by DBMS. In order to simplify it, we are able to have an instance of a company database where employee id is an attribute.
- Self-Describing Nature: Before DBMS, a standard file management process was used for saving data. and information there was no idea of characterization in traditional file management process like we’ve in DBMS. A DBMS must be of Self-describing nature as it not just includes the database itself but additionally the metadata.
- Support ACID Properties: Any keys in DBMS is in a position to help Durability, Isolation, Completeness, and ACID(Accuracy) properties. it’s made certain in each and every keys in DBMS that the true objective of information shouldn’t be lost while executing transactions such as delete, insert, and update.
- Concurrent Use of Database: There are chances that are many that a lot of people will be accessing the information at the exact same time. They might require altering the database process concurrently. At that moment, keys in DBMS support this concurrency, and the economic climate of the method could be enhanced.
- Insulation Between Program and Data: Program-data independence offers a huge help to website users. In a regular file management process, the framework of information files is identified in the application applications which are utilizing that certain details files.
- Transactions: Transactions are a lot of measures that are carried out to bring the database from 1 regular condition to a new constant state. Traditional file-based methods didn’t have the feature. The transaction is definitely atomic this means it is able to certainly not be further split. It is able to just be finished or perhaps uncompleted.
- Data Persistence: Persistence means if the information isn’t removed explicitly then all of the information will be taken care of keys in DBMS around. If any method failure occurs subsequently the life span of information kept in the DBMS will be determined by the people indirectly or directly.
- Recovery and Backup: There are lots of possibilities of failure of the entire database. At that time nobody is going to be able to obtain the database again and the certain business will be at a huge loss. The sole answer is to take a backup of the data source and anytime it’s required, it could be saved back.
- Data Integrity: This is among the most important attributes of the database management process. It shields unauthorized access to the data source and also causes it to be more secure. It creates accurate and consistent only details in the database.
- Multiple Views: Owners are able to have several views of the database based on their in
terests and department. Keys in DBMS support numerous views of the data source to the visitors. - Stores any Kind of Data: A database management system must be in a position to keep some data type. It shouldn’t be restricted to the worker’s name, salary, and address. Any type of information which is present in real life can be kept in DBMS since we have to work with all sorts of data that are present around us.
- Security: Keys in DBMS provides protection to the information stored in it because all the users have various rights to use the database. Several people are able to use a tiny portion of the database.
- Represents Complex relationship between Data: Information stored in a database is associated with one another and a connection is created between data. DBMS must be in a position to stand for the complicated relationship between information to make accurate and efficient utilization of information.
- Query Language: Queries are used to access and manipulate information but DBMS is armed with a good query language which makes it much more powerful and economical. Owners have the energy to access some data type they really want from the database by implementing various sets of queries.
- Cost: The price tag on the DBMS is significant as compared to the various other software program and technology readily available in the marketplace. But in case you think about the long term then DBMS is way much better since the maintenance cost of it is going to be practically nothing.
Components of DBMS

The DBMS could be divided into 3 principal parts. These are the information dictionary, the information characterization language, and also the information manipulation language. Data dictionary: The information dictionary is a focus of metadata.
The 5 main parts of a database are hardware, software program, data, process, and database access language.
- Storage engine
- Query language
- Query processor
- Optimization engine
- Metadata catalog
- Log manager
- Reporting and monitoring tools
- Data utilities
- Storage Engine: The storage motor is the primary element of the DBMS which interacts with the filing process at an OS degree to store information. All SQL queries which communicate with the basic information go throughout the storage engine.
- Query Language: A database access language is necessary for mingling with a data source, from producing databases to simply inserting or perhaps retrieving information. A suitable DBMS must support one or even a number of query languages and word dialects. Structured query words (SQL), and MongoDB Query Language (MQL), are 2 query languages that are used to work together with the databases.
In most query languages, the query words function could be further categorized according to certain tasks:
- Data Definition Language (DDL) – This is made up of instructions that may be used to explain database schemas or even change the framework of database objects.
- Data Manipulation Language (DML) – Commands that exclusively deal with the information in the database. All CRUD companies are available under DML.
- Data Control Language (DCL) – This deals with using the permissions along with other access controls of the repository.
- Transaction Control Language (TCL) – The command deals with inner database transactions.
- Query Processor: This is the intermediary between the end-user queries and the database. The query processor interprets the queries of owners and makes them actionable commands which could be known by the database to do the proper functionality.
- Optimization: The optimization Engine enables the DBMS to offer insights into the overall performance of the database in conditions of optimizing the data source itself and queries. When fused with database monitoring equipment, it is able to offer a strong toolset to obtain probably the best performance from the database.
- Metadata Catalog: This’s the centralized catalog of all of the items within the database. When an object is produced, the DBMS keeps a history of that object with a bit of metadata about it utilizing the metadata catalog. Next, this particular record could be utilized to:
- Verify user requests to the proper database objects
- Present an overview of the total database structure
- Log Manager: This component will keep all the logs of the DBMS. These logs will consist of user logins and activity, database functions, backups and restore functions, etc. The log manager ensures all these logs are properly recorded and easily accessible.
- Reporting and Monitoring Tools: Monitoring and reporting tools are another standard component that will come with a DBMS. Reporting equipment will allow people to produce reports while monitoring devices enable overseeing the databases for resource use, pc user activity, etc.
- Data Utilities: Besides each of the above, many DBMS application comes with extra inbuilt utilities to offer functionality such as
- Data integrity checks
- Backup and restoration
- Simple database repair
- Data validations
Advantages of Keys in DBMS

Keys in DBMS were released to resolve the basic problems connected with storing, securing, accessing, managing, and auditing information in standard file systems. Software users and organizations are able to achieve the following advantages by using the keys in DBMS:
- Improved Information Security: DBMS has the capability to manage users and implement policies for security and compliance control. This controlled user access raises the database protection and makes the information much less weak to security breaches.
- Simple Information Sharing: DBMS allows users to use the database properly regardless of their location of theirs. As a result, they can deal with any database-related task faster without the necessity for complicated access methods or even stressing about database security.
In addition to that, keys in DBMS allow multiple people
to collaborate efficiently when interacting with the repository.
- Data Integration: DBMS enables users to obtain a centralized view of directories dispersed across several locations and control them using a single screen rather than running them as individual entities.
- Abstraction & Independence: Keys in DBMS allows users to alter the actual physical schema of a data source without altering the rational schema that governs repository relationships. As a result, businesses are able to scale the underlying repository infrastructure without impacting the database operations. In addition, any shift to the rational schema can additionally be completed without affecting programs that use the databases.
Streamlined backup and healing mechanism Most databases have built-in backup and recovery equipment. Nevertheless, DBMS offers centralized resources to facilitate backup and recovery performance much more handily and thereby provide a much better user experience. Securing information is now easier than ever with features like
- Automatic snapshots
- Backup scheduling
- Backup verifications
- Multiple restoration methods
- Uniform Management and Monitoring: DBMS has a single screen to carry out all of the management and monitoring projects, therefore simplifying the workload of the repository administrators. These chores are able to range from database development and schema modifications to reporting and auditing.
- DBMSs are essential: DBMSs are a crucial part of just about any business when it comes to taking care of databases. The weighing machine, complexity, and characteristic pair of a DBMS will rely on the precise DBMS and demands of the businesses.
With various DBMS providing various feature sets, it’s paramount that organizations rigorously assess the DBMS application before committing to a one-time phone system. Nevertheless, a correctly configured DBMS will significantly simplify the management and maintenance of databases at every scale.
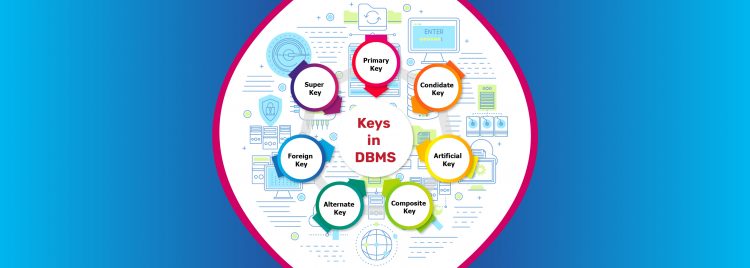
Types of Keys in DBMS
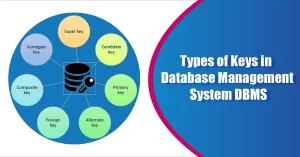
There are broadly 7 types of keys in DBMS:
- Primary Key
This is the main key of all the keys in DBMS. It is a column of a set or a table a pair of columns that helps to determine every record present in this table uniquely. There can easily be just one main Key on a dining room table. Furthermore, the main Key can’t hold the exact same values saying for any row. Every importance of the main element has to be completely different with no repetitions.
Primary Key (PK) constraint placed on a column or a set of columns won’t permit them to have some null values or any duplicates. One table is able to have just one main key constraint. Any worth in the main element can’t be transformed by any overseas keys (describe below) that refer to it. For example, in the table below, CustomerNo, which displays the ID number assigned to different customers, is the primary key. - Candidate Key: In terms of keys in DBMS, Candidate keys are those characteristics that uniquely identify rows of a dining room table. The Primary Key of a dining room table is selected from 1 of the applicant keys.
So, prospect keys have exactly the same qualities as the main keys discussed above. There can easily be over 1 candidate key on a dining room table. The minimum set of characteristics that will exclusively determine a tuple is recognized as a candidate key.
For instance, STUD_NO in Pupil relation. The value on the Candidate Key in keys in DBMS is non-null and unique for each tuple. Generally, there can easily be over one candidate key in a relation. - Super Key: Super Key is the set of all of the keys in DBMS which help identify rows in a table exclusively in keys in DBMS. What this means is that all of the columns of a dining room table then able to identify the various other columns of that dining room table uniquely and will all be seen as great keys. Super Key is the superset of an applicant crucial (describe below).
The Primary Key of a dining room table is picked from the great ingredient set to be created the table’s identity feature. A Super Key is a mix of columns that exclusively identifies some row inside a relational database management system (RDBMS) table. An applicant key is a strongly related idea in which the Super Key is reduced to the least amount of columns needed to exclusively determine each row. - Foreign Key: Foreign Key is used to build relationships between 2 tables in keys in DBMS. A foreign element is going to require each worth in a column or a set of columns to complement the primary Key of the referential table. Foreign keys in keys in DBMS help to preserve information and referential integrity.
A different key is a column or a team of columns of a relational database table that offers a link between information in 2 tables. It’s a column (or columns) that references a column (most usually the main key) of an additional table. - Composite Key: A composite key is a set of 2 or more characteristics that help determine each tuple in a kitchen table uniquely in keys in DBMS. The characteristics in the set might not be special when considered individually.
Nevertheless, when consumed altogether, they are going to ensure uniqueness. A composite element of SQL may be described as a mix of several columns, and those columns are utilized to find all of the rows which are required uniquely. While a single column cannot recognize some row exclusively, a mix of more than one column can exclusively recognize some record. - Alternate Key: As explained above, a table is able to have several options for the main key; however, it is able to choose just one. And so, all of the keys which didn’t turn into the main Key are called alternate keys. Alternative keys are those applicant keys that are not the main element.
Generally, there can easily be just one Primary element for a table. Thus all of the remaining Candidate keys are referred to as Secondary or alternate keys in keys in DBMS. - Unique Key: A unique Key is a column or a set of columns that uniquely identify each history in a table in keys in DBMS. All values are going to have to be distinctive in this particular Key. A distinctive Keys in DBMS differs from the main element since it is able to have just one null value, whereas the main Keys in DBMS can’t have any sort of null value.
A distinctive key is a column or a set of columns that exclusively recognize each history in a table. All values are going to have to be distinctive in this particular Key. A unique Key in keys in DBMS differs from the main element since it is able to have just one null worth, whereas primary keys in DBMS can’t have any null values.
Why are the keys in DBMS necessary
A keys in DBMS are utilized in the definitions of different types of integrity constraints. A table in a data source belongs to a set of events or records for a specific relation. Today there could be thousands and thousands of such documents, several of which could be duplicated.
There must be a strategy to
determine each record uniquely and separately, i.e. absolutely no duplicates. Keys in DBMS permit us to be totally free from this particular hassle. Keys are a significant element of table-level integrity and relationship-level integrity.
For example, keys in DBMS allow you to make certain that a table has special documents and that the areas you utilize to build a connection involving a pair of tables usually contain matching values. They work to set table relationships.
What are the Different Types of Keys in DBMS?
There are many kinds of keys in DBMS that are used in databases. The main keys in DBMS are utilized to determine a certain row in a table. The distinctive key is utilized to make certain that there’s just one entry in a certain table. Different keys in DBMS are utilized to link entries in a single table to yet another.
Composite keys in DBMS are a set of several columns in a table that altogether are used to determine a row. These keys in DBMS allow you to recognize a certain column of a row of a table uniquely and accurately. Hence, it’s really important to make use of the correct columns as the key as per your use situation of yours.
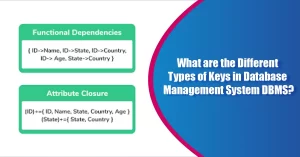
Functional Dependency
Functional Dependency (FD) is a constraint that establishes the relation of 1 feature to the next feature inside a Database Management System (DBMS). Functional Dependency helps you to keep the quality of details in the database. It plays an important role to find the big difference between bad and good database design.
A Functional dependency is a connection between attributes. In functional dependency, we are able to get the worth of an additional attribute from the provided feature. For instance, If we understand the importance of pupil roll numbers, we are able to get pupil addresses, marks, and so on.
Attributes
Generally, an attribute is a characteristic. In a database management product (DBMS), a character describes a database component, like a table. It also could relate to a database field. Attributes explain the cases in the column of a repository. Characteristics can additionally be subdivided into an additional set of characteristics. There are 5 such kinds of attributes: Derived, Multi-valued, Single-valued, Composite, and Simple attribute. Yet another feature is their, i.e. Complex Attribute, this’s the seldom-used attribute.
Attributes of Keys in DBMS are a characteristic or a set of attributes that allow you to determine a row(tuple) in a relation(table). They let you search for the relation between the 2 tables. Keys help you exclusively recognize a row at a table by a mix of one or more columns in this table
Closure of a set of Attributes in keys in DBMS
In mathematics, the closure of a subset S of areas in a topological room consists of all the points in S combined with all-cap areas of S. The closure of S might equivalently be identified when the union of S and the boundary of its, and as the intersection in the world shut sets that contain S.
The closure of a pair of characteristics X is the set of those characteristics which could be functionally decided from X. The closure of X is denoted as X+. When provided a closure issue, you will have a set of purposeful dependencies over which to calculate the closure along with the set X for what to discover the closure.
- In order to find attribute closure of a characteristic set: Add components of the feature set to the outcome set.
- Recursively add components to the outcome set which may be functionally decided from the components of the result set.
What are the various types of keys in DBMS?
There are many kinds of keys employed in a database. The main keys in DBMS are used to determine a certain row on a kitchen table. The unique key is used to make certain that there’s just one entry in a certain table. A foreign key is utilized to link entries in a single table to yet another.
A composite key is a set of several columns in a dining room table that all together are accustomed to determining a row. These keys allow you to recognize a certain column associated with a row of a kitchen table uniquely and accurately. Hence, it’s really important to make use of the correct columns as the key as per your use case of yours.
Conclusion
Keys in DBMS are only a means to exclusively determine each table’s record. Learned about the great element and the way to look for candidate keys from it. We select one secret from a set of candidate keys like the main element and brand any other keys as alternative keys.
Keys and purposeful dependencies play a really crucial role in developing a database. These ideas likewise aid in finding the big difference between bad and good database design. The last practice of removing redundancies and making the database effective is normalization, which uses all ideas talked about in this document.
Frequently Asked Question’s
The main key element is utilized to determine a certain row in a table. The unique key element is utilized to make certain that there’s just one entry in a certain table. A different key element is utilized to link entries in a single table to yet another. A composite key element is a set of several columns in a table that altogether are used to determine a row.
The key is an area, or maybe a combination of fields, in a database table used to access and sort rows in the table based on needs that are. Keys are identified to accelerate access to data and also, in instances that are most, to produce links between several tables.
3. What are the types of keys in DBMS?
- Primary Key: The main key is a column of a set or a table a pair of columns that helps to determine every record present in this table uniquely. There can easily be just one main Key on a dining room table. Furthermore, the main Key can’t hold the exact same values saying for any row.
- Candidate Key: Candidate keys are those characteristics that uniquely identify rows of a dining room table. The Primary Key of a dining room table is selected from 1 of the applicant keys.
- Alternate Key: Alternative keys are those applicant keys that are not the main element. Generally, there can easily be just one Primary element for a table.
- Super Key: Super Key is the set of all of the keys which help identify rows in a table exclusively. What this means is that all of the columns of a dining room table then able to identify the various other columns of that dining room table uniquely and will all be seen as great keys.
- Composite Key: A composite key is a set of 2 or maybe more characteristics that help determine each tuple in a kitchen table uniquely.
- Foreign Key: Foreign Key is used to build relationships between 2 tables. A foreign element is going to require each worth in a column or maybe a set of columns to complement the primary Key of the referential table.
- Unique Key: A unique Key is a column or maybe a set of columns that uniquely identify each history in a table. All values are going to have to be distinctive in this particular Key.
4. What is super keys in DBMS?
In the relational information model, a Superkey is a set of attributes that uniquely identify each tuple of a relation. Because superkey values are unique, tuples that have the same superkey value should also have exactly the same non-key attribute values. That’s, non-key attributes are functionally determined by the superkey.
A main key element is a column or maybe columns that have values that uniquely identify each row in a table. A database table should have the main key for Optimum to insert, restore, update, or perhaps delete data from a database table.
6. What is difference between primary key and composite key?
While the main key and a composite key could do exactly the same issues, the main key will consist of one column, the place that the composite key will consist of 2 or maybe more columns. The connection between the main key and a different key is pretty different.
7. What are the 4 types of DBMS?
4 kinds of DBMS (database management systems) are
- Hierarchical Database Systems: Working in a format that is based on the product of the parent-child tree, hierarchical DBMS are very great for saving info with products that describe characteristics, characteristics, and any other such items.
- Network Database Systems: Similar to hierarchical DBMS, this particular method has numerous parents to a lot of relation models. The networking version structure uses SQL because of the manipulation of information which could in turn be implemented to acquire valuable insights and learnings.
- Object-Oriented Database Systems: Objective-oriented DBMS of several structures that are rather extensive in nature. This particular design is based on the performance that information and its concerning object are viewed as a single device.
- Relational DBMS: One of the more famous DBMS, offered in the marketplace is known as relation DBMS since they’re super easy and very simple to use. These methods are normalized by using information that is commonly saved in tables.
Several examples of popular database software programs or maybe DBMSs include
- MySQL
- Microsoft Access
- Oracle Database
- Microsoft SQL
9. What are the component of DBMS?
Hardware, Software, Data, Database Access Language, Procedures, and Users all together create the parts of a DBMS.
- Storage engine: The storage motor is the primary element of the DBMS which interacts with the filing process at an OS degree to store information.
- Query language: A database access language is necessary for mingling with a data source, from producing databases to simply inserting or perhaps retrieving information.
- Query processor: This is the intermediary between the end-user queries as well as the database. The query processor interprets the queries of owners as well as makes them actionable commands which could be known by the database to do the proper functionality.
- Optimization engine: The optimization Engine enables the DBMS to offer insights into the overall performance of the database in conditions of optimizing the data source itself and queries.
- Metadata catalog: This’s the centralized catalog of all of the items within the database. When an object is produced, the keys in DBMS keeps a history of that object with a bit of metadata about it utilizing the metadata catalog.
- Log manager: This component will keep all the logs of the DBMS. These logs will consist of user logins and activity, database functions, backups and restore functions, etc. The log manager ensures all these logs are properly recorded and easily accessible.
- Reporting and monitoring tools: Monitoring and reporting tools are another standard component that will come with a DBMS. Reporting equipment will allow people to produce reports while monitoring devices enable overseeing the databases for resource use, pc user activity, etc.
- Data utilities: Besides each of the above, many DBMS application comes with extra inbuilt utilities to offer functionality such as: Data integrity checks, Backup and restoration,Simple database repair, and Data validations.